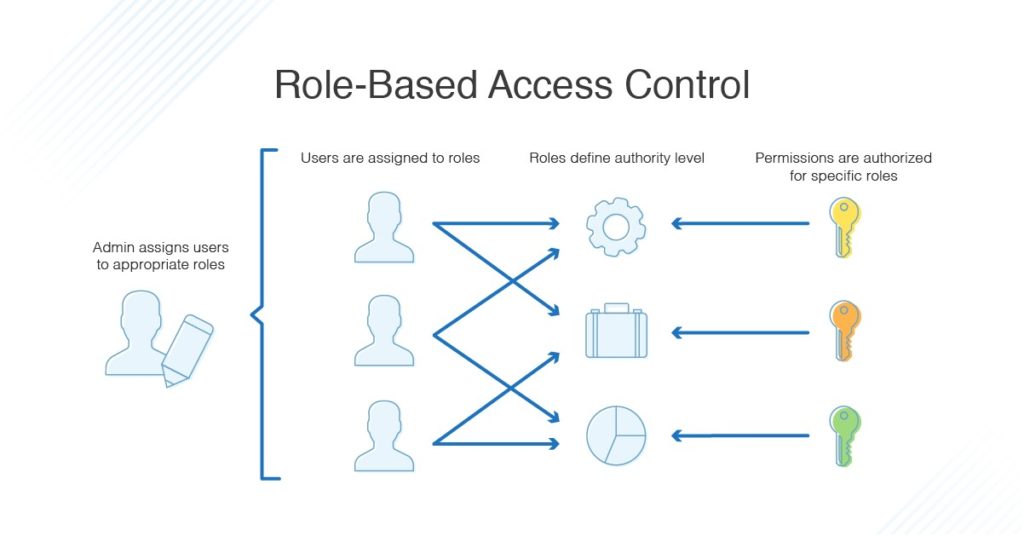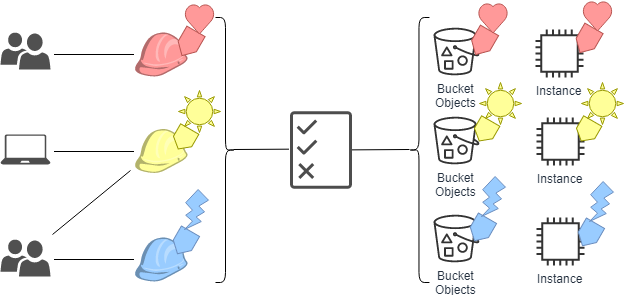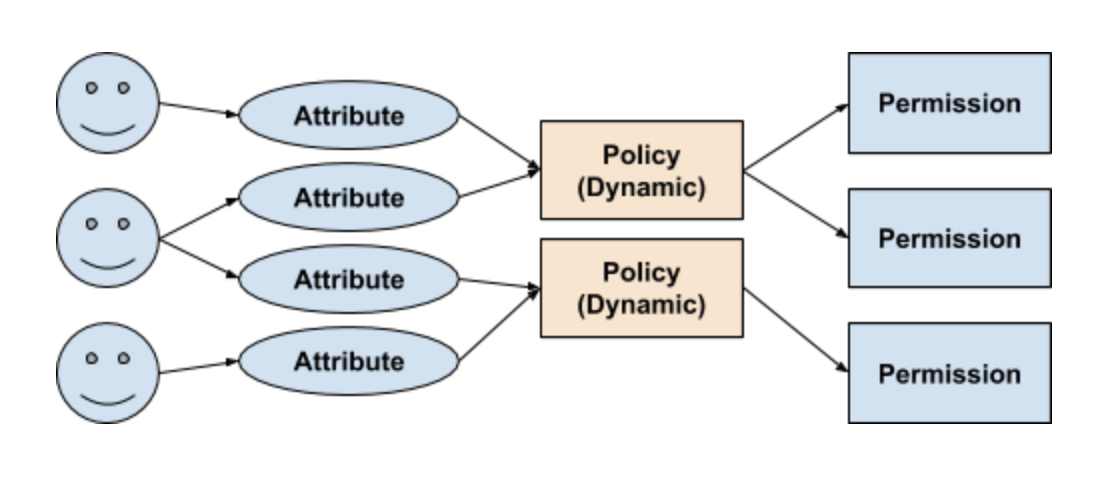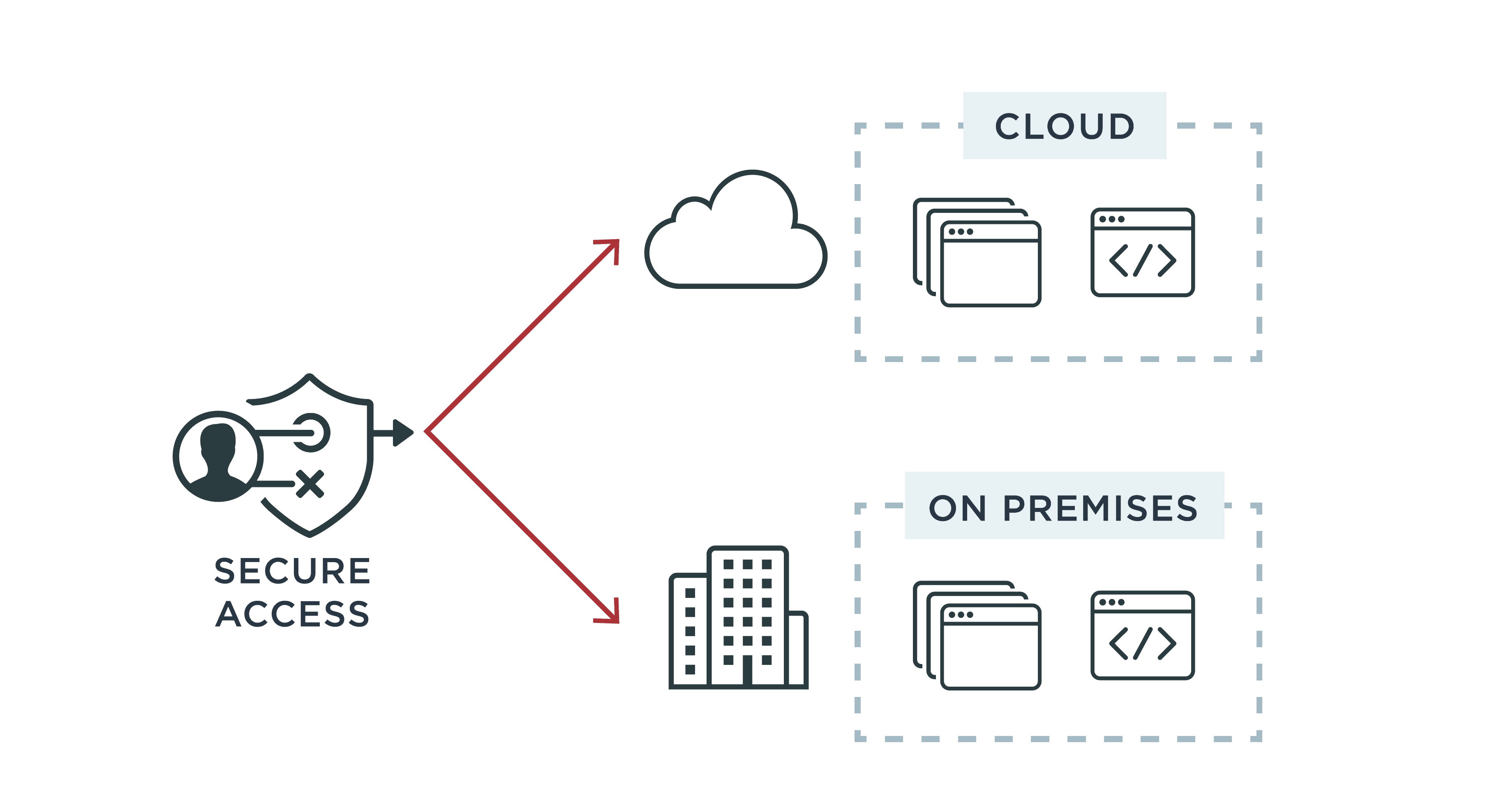
Role-based Access Control (RBAC) vs. Attribute-based Access Control (ABAC) : What's the Difference? | Ping Identity
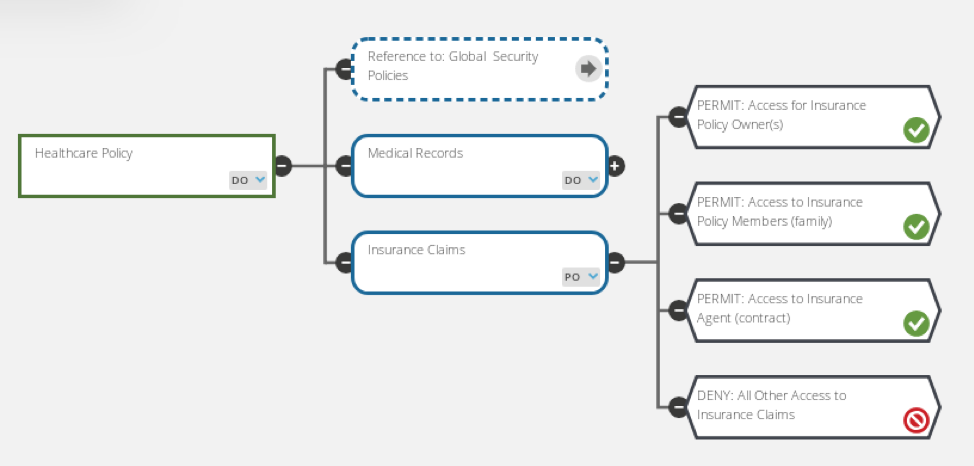
Why Attribute-Based Access Control Will Become the Standard Model for Large Enterprises - DZone Security

Research Summary: Efficient Attribute-Based Smart Contract Access Control Enhanced by Reputation Assessment - Auditing and Security - Smart Contract Research Forum

permissions - What is a suggested roadmap towards implementation of a simple Attribute-based access control (ABAC)? - Software Engineering Stack Exchange


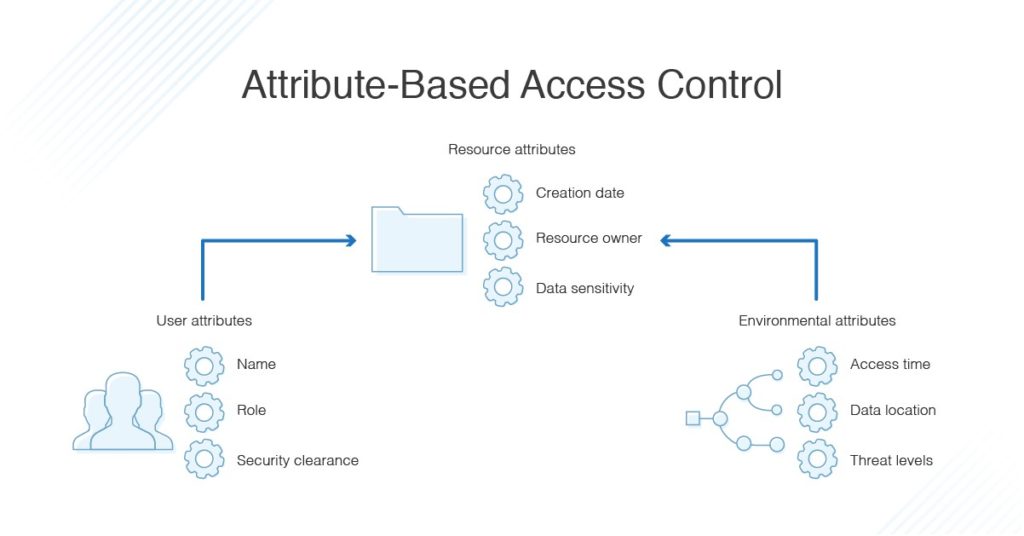

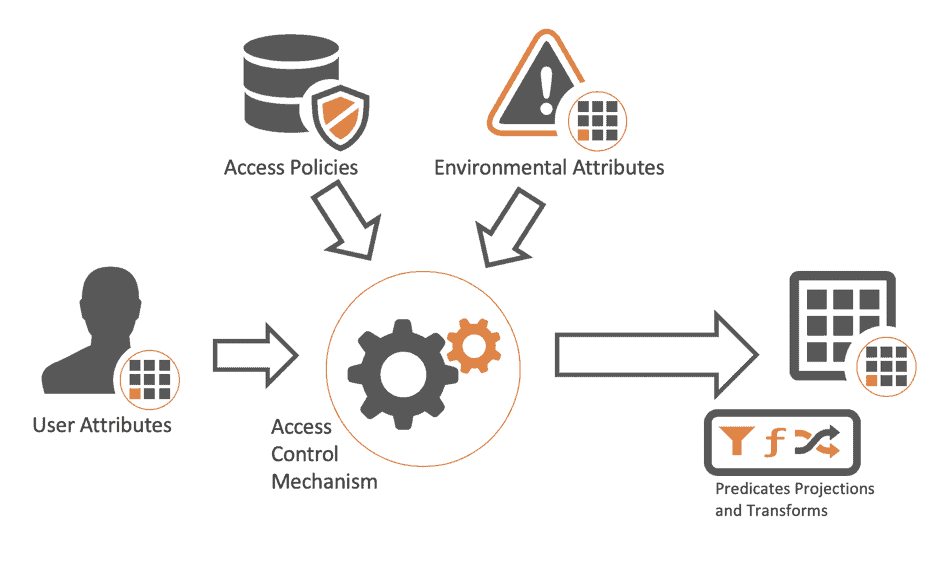
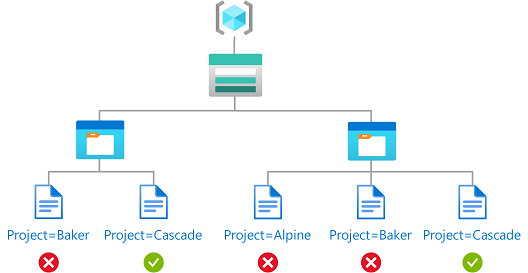
![PDF] Attribute-Based Access Control | Semantic Scholar PDF] Attribute-Based Access Control | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f2d698c5a1819b0cff0c8899b8a391c5721aa2b6/2-Figure1-1.png)