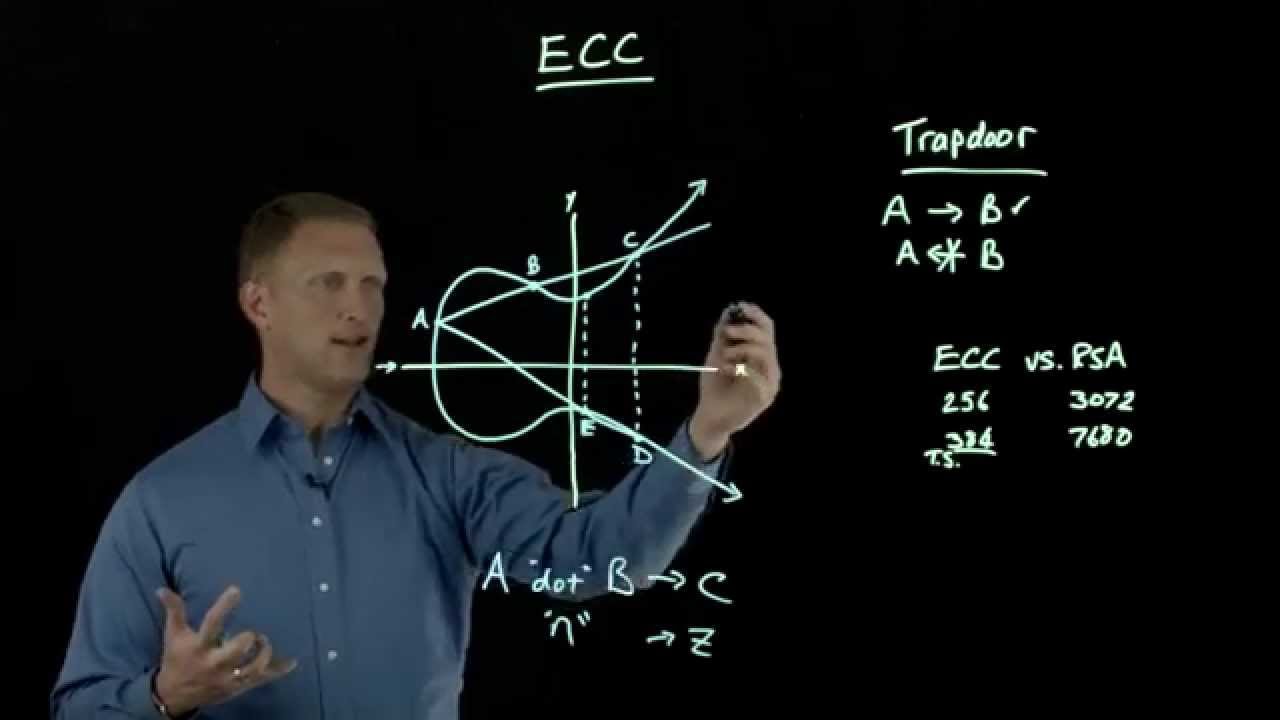
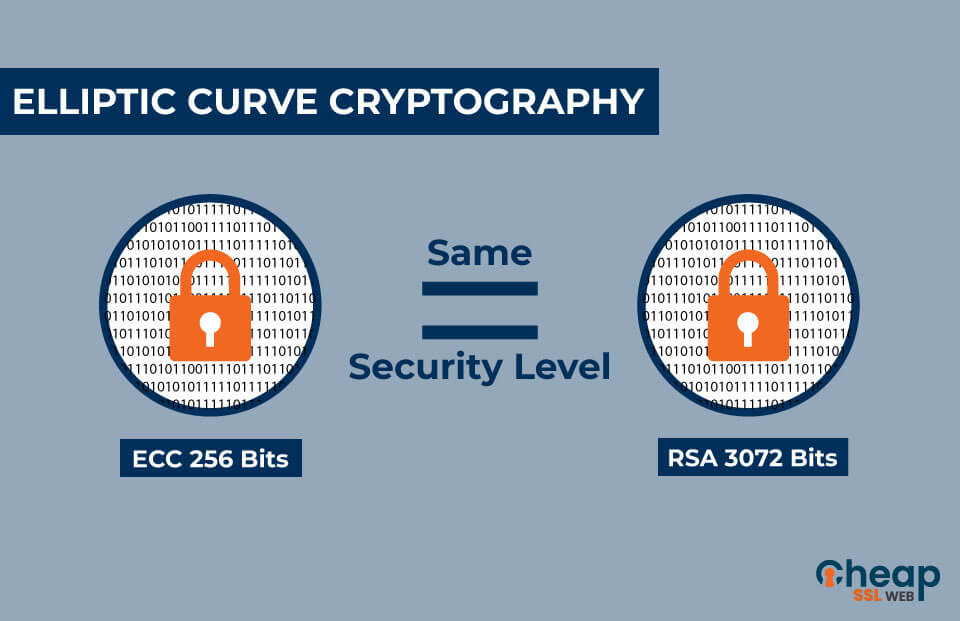
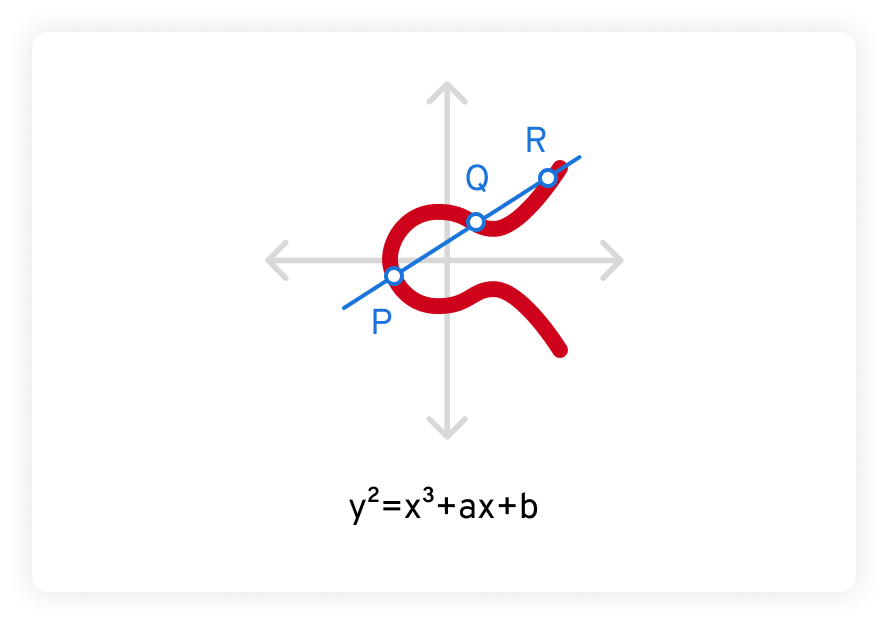
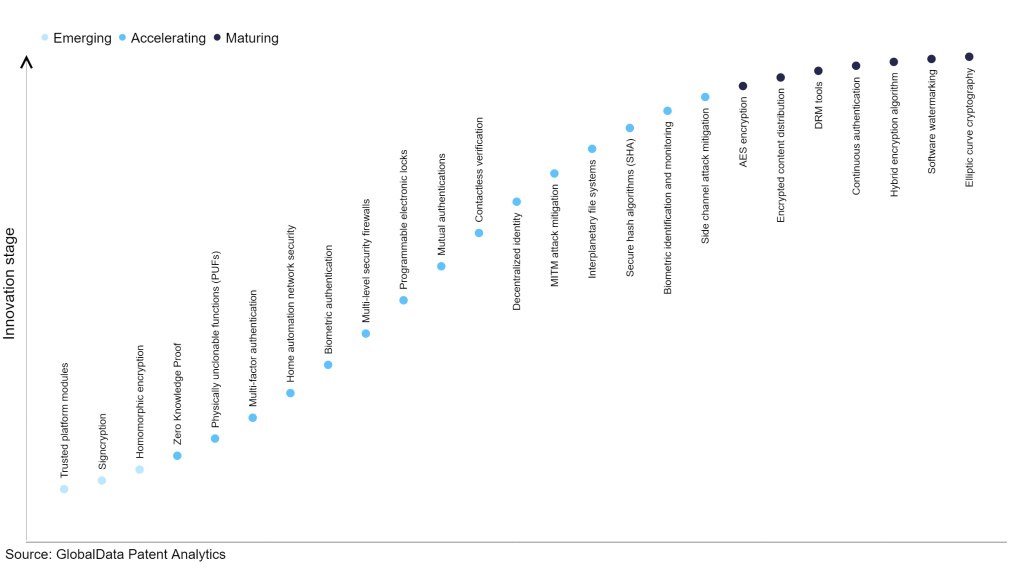
ECC Algorithm to Enhance Security with Better Key Strength | Algorithm, Security, Cryptography algorithms
ComplyAdvantage and Elliptic Partner To Develop Blockchain Analysis and Transaction Monitoring Tool | The Fintech Times

Elliptic answers growing demand for blockchain intelligence and crypto identity with US public sector expansion

Waikato students take out the grand prize for the NZ Cyber Security Challenge - News and Opinion: University of Waikato

Elliptic and BlockTrace Forge Strategic Partnership to Bolster National Security in the Digital Asset Realm